Small Business Cybersecurity
A Detailed Guide To Protecting Your Company & Employees
Locking down your data is absolutely essential in today’s digitally-focused business environment.
Today, the “data economy” means that data is the most valuable resource in the world – and cyber-attacks are becoming more costly and more expensive than ever. And according to IBM, a data loss or hack at your business can be extremely costly, with an average cost of $3.86 million in 2020 alone. According to that same study, around 52% of data breaches are caused by malicious attacks – which are growing in prevalence every year. Hackers want to:
- Interrupt your business.
- Steal your identity.
- Lock down your data with ransomware to get a monetary reward.
- Sell the information they steal – such as credit card details or other identity-related information – to the highest bidder on the dark web.
How can you stop or at minimum prevent these types of attacks?By
- Adopting proper password protections at your business.
- Knowing how to identify email phishing and social engineering attacks.
- Being on guard while browsing the internet.
In this guide, we’re doing to discuss the main actions you can take protect yourself, your employees, and your organization from data loss.
Thanks for Reading,

Eric Clemens, CEO
Acroment Technologies
What Entry Points Do Hackers Target When Attacking Businesses?
Let’s start with the basics. How do hackers steal your information? What entry points or “vectors” do they use to steal data? There are dozens of different ways – but the vast majority of data breaches occur through a few common entry points.
- Weak or reused passwords – Weak passwords are a huge point of vulnerability, particularly if you or your employees reuse passwords in your professional and personal life. Hackers who breach a personal email, for example, may be able to use that same password to get into corporate systems if you’re re-using a weak password.
- Email – Email “phishing” attacks are responsible for a staggering volume of data loss. Verizon estimates that up to ⅓ of all data breaches are related to phishing.
- Social engineering – Social engineering, such as getting someone to disclose personal information about your company over the phone, is a major attack vector.
- USB/other media devices – Some hackers may leave USB drives and other media devices lying around in public places, hoping that someone picks them up and plugs them into their computer. Never plug any unknown device into your computer.
- Software vulnerabilities – Hackers can exploit vulnerabilities in web browsers, operating systems, and other software to steal data, but this is not a huge threat as long as you keep your systems updated.
Passwords – Your First Line Of Defense Against Data Theft
Wondering how you can protect yourself against data theft? Passwords are always going to be your first line of defense. Until there’s some other kind of way to truly authenticate your identity (biometrics like facial recognition are getting close), passwords are the best way to confirm that you’re actually… you!
But it may be easier for hackers to guess your passwords than you think. Ask yourself the following questions before you read on:
- Do you store your passwords in documents or spreadsheets (on your computer or online)?
- How secure/complex do you believe your passwords are?
- Do you use the same password on multiple sites?
- When was the last time you changed your passwords?
How do hackers get your passwords?
Let’s start by talking about how hackers get your passwords. The most common way is with a “brute force” attack. What this means is that a hacker sets up a special computer that uses a device to “crack” your password by guessing billions of different variations every second.
Yes, billions. Even using consumer-grade hardware, a hacker could create a system that can guess 350 billion passwords per second in 2012 – and more modern computer hardware is even faster.
Once they’re set up to crack a password, hackers dump databases from hacked sites, common passwords, social data, and other information into the system – and then they run it until it identifies the password.
So how can you protect yourself against this? With a strong password.
Understanding Password Strength
Passwords are created using a combination of 94 different characters, which include:
- Numbers 0 – 9
- Uppercase Letters A – Z
- Lowercase Letters a – z
- Symbols: ~!@#$%^&*()_-+=[{]}\|;:’”,<.>/?
The number and variety of these characters ultimately determines how long it will take to crack your password.
Password “strength” (or password entropy) refers to how unpredictable your password is. It is measured in bits. For perspective, a known password has 0-bits of entropy.
For every additional character you include in your password, you exponentially increase the possible combinations a hacker will have to try to guess your password.
For example:
- A four-character password of numbers only includes 10,000 possible combinations. This would take a computer milliseconds to test each option.
- An 8-character password using only upper and lowercase letters includes 200 billion possible combinations. At 100,000,000 guesses per second, it’d take 30 minutes to crack that password.
- An 8-character password using numbers, upper and lowercase letters, and symbols has 7.2 quadrillion possible combinations. This would take over 2 years to guess. (source)
As you can see, the more characters and the greater the variety, the longer your password takes to guess.
How to create a strong, modern password
So, what does a “good” password look like? The web comic XKCD has a great example. In this comic, two passwords are compared.
- Tr0ub4dor&3. This password has 28 bits of entropy. By today’s computational standards, this is considered a weak password.
- correct horse battery staple – This has 44 bits of entropy. This is a reasonably strong password.
CorrectHorseBatteryStaple Passwords
The format we recommend, then, is simple. As in the above example, you should take four, 5-7 letter words that are unrelated and uncommon, and don’t have a relationship to one another. Then, use this as your password!
Try to mix up your word choice by using words not found in the dictionary, as dictionaries can be fed into a computer for brute force attacks.
Obscure brand names and technical terms are great options!
Basically, the length of your password is a lot more important than the special characters you use. And while some services and websites may still require you to swap in special characters, capitals, and symbols, you can simply add these to your preferred password when necessary.
The Old Tricks Don’t Really Work Any More
If you’ve ever signed up for a new account on a website, you may have seen a little pop-up near the login section that tells you how strong your password is – and that you can strengthen it by adding special characters like ! @ # $ %, CaPiTaL LeTtErS, or by using numb3rs in the place of a few letters. But in reality, these steps don’t help strengthen your password at all. And here’s why.
Anyone trying to breach your password will know that “best practices” involve adding capital letters, swapping numbers for letters, and other such steps. So all they have to do is program their equipment to accommodate these rules – for example, swapping the letter “i” with “1”. This takes milliseconds to try, and can be repeated hundreds of times with different rules, dictionaries, and other such information. This means that those “strong” passwords may not be as strong as you think. Not only that, they’re hard to remember.
Further recommendations for password security
Beyond simply using a secure password, there are a few more ways you can lock down your password and improve security.
- Password managers like LastPass – LastPass and similar password management programs automatically generate secure passwords, save them for use on your computer, and encrypt them to protect them locally. They are extremely secure, and allow you to keep your information very safe, though it may take some time to adjust to this new system.
- Multi-factor authentication – Multi-factor authentication or MFA for short, also known as “2 factor authentication” or 2FA is a method of protecting you even if a hacker finds your password. After you enter your password, you use an app from Microsoft or Google that generates a random code, or a dedicated device like a Yubikey. Then, you enter this along with your password to confirm that you’re really yourself. MFA should be always used for very sensitive data, such as corporate logins, bank data, Google, Facebook, and anywhere else you can enable it.
- Avoid SMS 2FA – 2-factor authentication with SMS messaging is not secure, and should be avoided. Hackers can convince cell phone companies to change the phone number over to a new phone, then use it to gain access to your accounts. This is how Twitter got hacked in 2019! While SMS 2FA is better than nothing, it’s not as secure as using a dedicated app.
- Modern biometrics – Modern biometrics like fingerprint and facial recognition are becoming more advanced and common, and should be integrated into your IT security policies when possible. The iPhone’s Face ID is a great example of a biometric security feature.
- Don’t save default payment info in browsers – If a hacker gains access to your web browser, they may be able to find saved passwords, emails, and payment information in the browser. To safeguard against this, try to avoid saving default information and logins in your web browser.
- Check for leaked or vulnerable passwords – Websites like HaveIBeenPwned.com let you enter your email address and see if it has been included in any major data breaches. If it has, you may want to change your passwords.
A Quick Note about LastPass
Owning an IT services company and managing dozens of client accounts requires me to have a lot of logins. Out of 200+ logins I use, I know the username and passwords to only four. I use LastPass to manage the others.
The reason I chose LastPass over other password management tools is because LastPass is a “zero-trust” system. In other words, no one, not even employees, can access your passwords. You have to verify who you are before gaining access to the usernames and passwords in your account. It’s also the preferred choice for a lot of the cybersecurity experts I follow.
If you’re considering a password management system for your company or yourself, I’d start with LastPass.

Hackers Want Your Trust – Don’t Give It To Them!
So, we’ve discussed passwords. Now, it’s time to move onto another major attack vector, known as “phishing.” This is the act of a hacker posing as a trustworthy person or organization in order to infect your computer, steal your information, and generally get up to no good.
Above all, hackers want you to trust them. So don’t. You’ll see that this is a theme in this section. Always be skeptical about what you click, what you download, the phone calls you get, and the emails you receive. It always pays to be careful.
Email Attacks Or “Phishing”
The most common type of trust-based attack is an email attack, also known as “phishing.” Basically, this is an attack where someone tries to trick you into clicking an email that looks legitimate – but actually will steal your information, install a virus onto your computer, or take some other kind of malicious action.
There are a lot of ways to combat phishing, but one of the easiest ways is to always check the address of each link. Oftentimes, hackers will try to “spoof” a legitimate link, but if you look carefully, you can tell the difference.
Website links are broken into 3 parts:
- A subdomain, such as www.
- A domain name, such as Amazon
- A top level domain (TLD), such as .com.

Put those together, and you have www.amazon.com.
Now, let’s assume an email enters your inbox, claiming to be from Amazon. It says your recent order has shipped, and to click on a link for updates.
But the link actually points to the URL Amazon.com.order-status.jp, or a link like www.amaz0n.com – these are examples of fake URLs that may be part of a phishing attempt.
Phishing is such a popular way to steal information because it operates based on trust – you trust that you got a legitimate email, so you open it.
The other reason is that phishing is incredibly cheap. It costs a hacker basically nothing to send an email out to hundreds of thousands of people. And if even a few people fall for the phishing attempt, they stand to profit. Let’s take a deeper look at what phishing looks like now.
What Does Phishing Look Like?
Let’s take a look at a few examples of phishing to show you how it may look in practice, and help you recognize potential phishing attempts in the future.
Unexpected DocuSign email
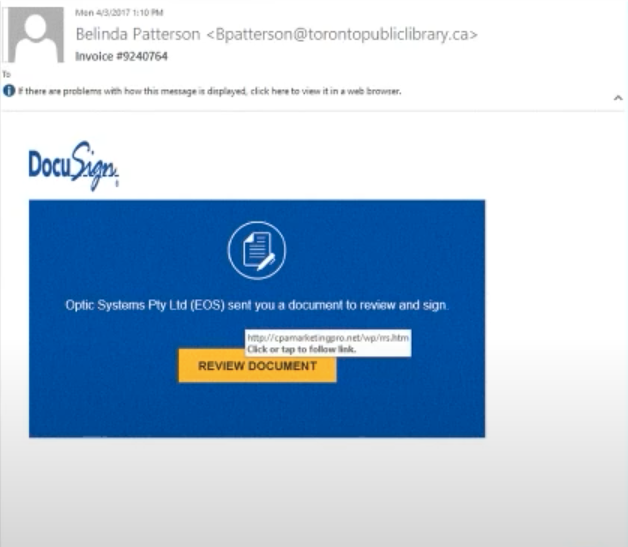
Initially, you might think this is a legitimate DocuSign email. But there’s a problem – you weren’t expecting a DocuSign email.
That’s your first warning. Why would you get a DocuSign email that you weren’t expecting? The second warning is that the link goes to “cpamarketingpro.net” – not a DocuSign address.
Always look carefully at these kinds of messages.
- Are you expecting a message?
- Do you know the sender?
- Where does the URL point to?
Knowing this can help you avoid a phishing attempt.
Enticing Headlines
Another common phishing attack is to send you an email with a link to a website – often with a scandalous or enticing headline. These can sometimes get through your spam filters, and may have links or attachments that could compromise your computer. As a rule of thumb, don’t click on an article or offer sent to your email if it looks suspicious.
Unusual sign-in activity
This is a very common way to phish users, especially in corporate environments. In one example, “Microsoft” sends you an email telling you that it has detected unusual activity.
But this is not an official email – remember, anyone in the world can get an Outlook.com email address. The sender “no-reply@mailteam2@outlook.com” is not an official Microsoft sender.
If you ever receive an email like this, you should always be suspicious. We recommend sending it to your IT department. Your IT team can open the link or attachment for you in a safe environment to see if it’s legitimate.
Email Safety Tips: Keep Yourself Safe From Phishing
Below, we’ve put together some email safety tips that will help you protect yourself and stay safe from phishing attempts.
- Forward suspicious emails to the helpdesk – If you’re at all suspicious about an email, forward it to IT so that they can check it and confirm whether or not it’s legitimate. It’s always better to be safe than sorry.
- Preview (never open) attached files – In some cases, you can preview files and attachments by clicking the attachment one time. However, do not open or save the file. Doing so could infect your computer. If you’re in doubt, just leave the attachment alone completely.
- Examine links and email addresses carefully – Checking the sender’s email address and the URLs and links in the email will usually be enough to determine if a message is legitimate or not, so always double-check these things in emails that seem suspicious.
- Ask senders about suspicious messages – If you get a message that seems strange from a coworker or supervisor, don’t just follow their instructions. Ask them about it. Why? A great real life example is one hacker posed as the CEO of a company, and asked the bookkeeper to wire $30,000 to an individual. The bookkeeper did it, thinking the request was legitimate – but it wasn’t. The company lost the money, and that could have been avoided if the bookkeeper had simply called or emailed the CEO directly to double-check his request. In another example, one individual had their email hacked. Hackers had access to the contacts, usernames, and passwords, and signatures of the company’s employees – then registered a domain name that was similar to the company name. They started emailing known customers, asking for payments on fake invoices – and many of these payments were made without the customers even realizing something was wrong.
- Log in without clicking links – It’s always a good idea to go directly to a certain website or service and log in without clicking a link sent to your email. If eBay says there’s a problem with your account, log into eBay. Don’t just click the message in your inbox.
- Look out for URL shorteners – URL shorteners like Bit.ly can hide long website links that may look suspicious on their own, so be wary of any email containing a shortened link.
- Call to verify – If you get an email from your bank, for example, call the bank directly to confirm the information, rather than clicking on the link. This lets you safely confirm whether the email was legitimate.
- Be suspicious of any unexpected mail – Any email you get that you didn’t expect could be an attack vector. Be vigilant, and always be suspicious of unexpected messages.
Other Common Phishing Vectors
While email is the most common way that hackers may attempt to phish you, there are other ways that your system could be compromised. Here are a few more examples.
Direct messages or instant messages on social websites
You should always be suspicious of direct messages on social websites, even if they look like they come from someone close to you – like your mother, child, partner, or close friend.
If someone’s Facebook gets hacked, for example, the hacker may send a phishing link to everyone on that person’s friend’s list in Facebook Messenger, in hopes that you’ll open the link since it’s coming from a familiar person.
Again, the same rules apply. Always be suspicious of unsolicited messages, and even if the message comes from someone you know, contact them directly to ask about it and confirm it’s legitimacy.
Calendar invitations
While this is not extremely common, there are ways attackers can injection appointments into your calendar without you knowing about it. Then, the time comes for the meeting, and you join a fake Zoom meeting, and the link you open could steal your data.
If you don’t remember scheduling a specific meeting, don’t click the link.
Vishing (voice phishing)
This is a very common type of phishing, and has grown hugely in the last few years due to the billions of robocalls made each month. Someone may pose as an employee of your bank, for example, and say there is a problem with your account in order to solicit information from you.
The best thing to do, especially if the person on the line is suspicious, is to hang up and call the institution back. If there really is an issue, they’ll know about it, and you can proceed from there.
SMishing
Fake text messages are very common from hackers posing as Google, Apple, Microsoft, and many other institutions. Just like a phishing email, SMishing is designed to fool you into clicking a dangerous link.

Protect Yourself With Safe Web Browsing
So, we’ve discussed passwords and phishing. It’s time to talk about another important step in protecting yourself and your company from data loss – safe web browsing. Here’s what you need to know.
Incognito is not a safety mechanism
Most web browsers offer an “incognito mode” or a “private mode.” This does not protect you from viruses or hackers. All it does is block “cookies,” tracking information, and history data in your browser. Even while browsing incognito, you’re just as exposed to risk as you would be if you were browsing normally.
Always be careful about what you download
Be wary about downloading free software, even if it’s something that seems legitimate and useful. Hackers and pirates often use free software or media downloads as a vector for viruses, malware, and identity theft. Remember – if an offer sounds too good to be true, it probably is.
Check for SSL
SSL (Secure Socket Layer) and its successor TLS (Transport Layer Security) are types of encryption that protect data you enter on websites. You can often check this in your browser’s address bar, and looking for a little padlock symbol, indicating that your data is encrypted. Do not shop or enter personal information on websites that do not encrypt your information properly.
Beware of ads
Ads are a very common attack vector for hackers and malicious actors, so be careful when visiting any website that uses ad networks.
Clicking on ads could bring you to unsafe sites, and it’s possible for your information to be stolen or for your computer to be compromised even if you don’t download anything. So, as a rule, don’t click ads when browsing the internet whenever possible.
Avoid unnecessary browser plugins
Web browser plugins can be useful and add more functionality to your web browser, but these programs can have security flaws, and could be used to steal your information. If you do install a browser plugin, make sure you verify its developer, its legitimacy, and its functionality before doing so.
Don’t save your passwords in your browser
As mentioned in the password security section, this makes it a lot harder for someone to commit fraud or steal your information if they gain access to your web browser. You should never save passwords in your browser.
The one exception is Apple’s macOS password system. This securely encrypts and saves passwords to your computer and iCloud, and is very safe to use.
Use a VPN on public WiFi networks
A VPN (Virtual Private Network) is a tool that creates an encrypted “tunnel” between your computer and the website you want to access. This secure link blocks anyone observing from seeing the data you’re sending, and dramatically enhances security.
Because of this, we recommend using a VPN whenever you’re on a public, unsecured WiFi network, such as when you’re working at Starbucks or staying at a hotel. While VPNs do usually result in slower internet speeds, the extra layer of protection is worth it.

Protecting Yourself From Threats In The Future
Unfortunately, as our world becomes more digitally-focused, the threat posed by hackers will only get worse. Malicious individuals are always looking for the “next big thing” that will allow them to steal corporate and personal data.
In the future, there may be even more threats that face individuals and businesses, including machine learning and AI, which can be used to create “deep fake” audio and video. For example, a hacker could pose as your boss and tell you to buy gift cards or send money to a particular address – and even imitate their voice and appearance to make the request seem legitimate.
Social networking is also likely to continue to be a major attack vector in the future, particularly as it becomes easier for hackers to “catfish” and trick people into adding them to their social networks.
There’s no way to tell exactly what threats lie in the future. But make sure to stay vigilant. Keep yourself safe, keep your business safe, and talk to your kids about internet safety, too. Follow the best practices we’ve outlined in this guide, and you’ll have better odds of protecting yourself from tomorrow’s threats.
The Bottom Line: Always Be Vigilant
Thank you for reading this guide from Acroment Technologies. If you’ve made it this far, you’re going to be able to protect your data much more effectively than most other people. So, what have we learned? What are the takeaways? Let’s boil it down.
- Think before you act – Above all else, think before you click a link, open an attachment, send an email, or do anything else. Hackers do not want you to think. They want you to obey, and blindly open whatever they send. So take the time to step back, and think critically about whatever you’re seeing. Chances are, you’ll recognize that it’s suspicious.
- Verify before you trust – If an email comes from IT, don’t just assume it’s from IT. Contact someone to verify it. This is the only way to truly know if the email or message is legitimate, and it’s always worth taking the time to perform this verification step.
- Be suspicious of anything you don’t expect – As a rule, if you get a message or email that you don’t expect, be suspicious, even if it looks legitimate. Why would you get a coupon to a store you’ve never shopped at? Why would you get an email from the CEO when you’ve never spoken? Why would IT tell you to send your password to them via email? When you’re suspicious, it’s easier to identify the inconsistencies and issues that reveal when you’re being phished by a hacker.
- Never assume something is safe – Always be vigilant. Hackers are constantly coming up with new ways to steal data. Don’t just assume that you can click a link and your computer won’t be infected with a virus. Until proven otherwise, anything you receive in your inbox or see online is a potential security threat.
- Understand that IT is just one layer of security – IT can’t filter out all spam or dangerous links. IT is only one layer of security, and while most IT teams can help cut down on suspicious messages, it’s up to you to provide additional levels of security, such as using strong passwords, being suspicious of sketchy links, reporting potential threats, and so on.
Have Questions About Your Security?
Defending your business and employees against cyberattack is a top priority. With the right plan, a knowledgeable partner, and constant awareness you can limit the threats we all face. If you have questions about the security of your organization, Acroment Technologies can help.


